Simple
Data Protection and Cybersecurity Unified
The Power of One
Being able to manage security using multiple tools is tiring and becoming less effective. Bluefin Technology Group simplifies this by using products that unify data protection and cybersecurity to protect your applications, data, and systems while lowering the risk of cyberattacks. This helps your business gain efficiency from automation of backup and recovery process, cyberattack prevention capabilities, vulnerability assessments, patch management, and more - all from one console.
Advanced Backup
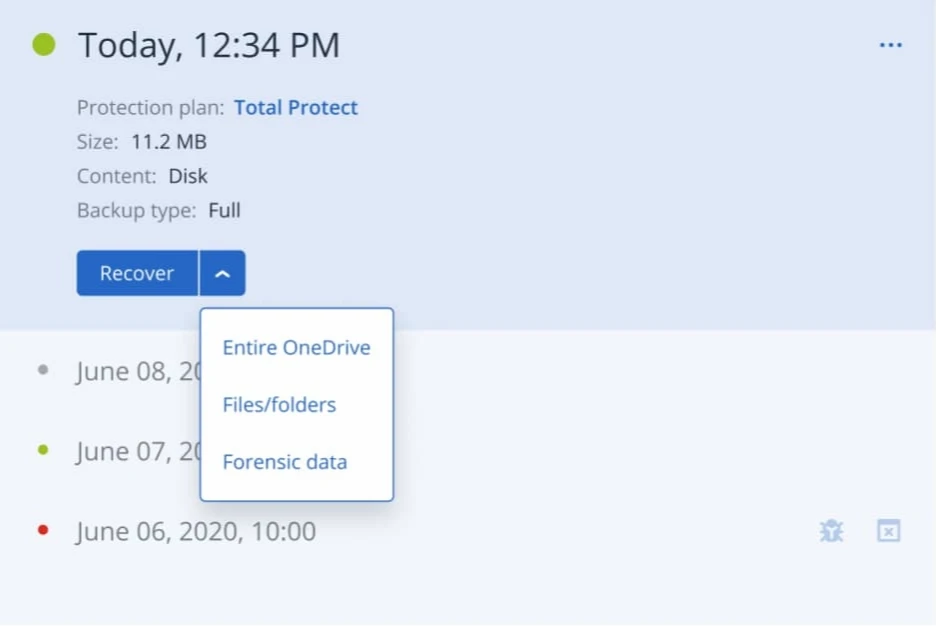
Eliminate downtime while protecting your business from advanced threats. Continuous data protection backs up changes made in real-time from business-critical applications so no data is lost.
Disaster Recovery
Get back to business in minutes when disaster strikes by spinning up your systems in the cloud ensuring immediate data availability. Make DR painless with orchestration, runbooks, and automated failover.
Data Loss Prevention
Prevent data leakage from workloads via peripheral devices and network communications. Automatic initial DLP policy creation allows accurate and efficient business-specific policies.
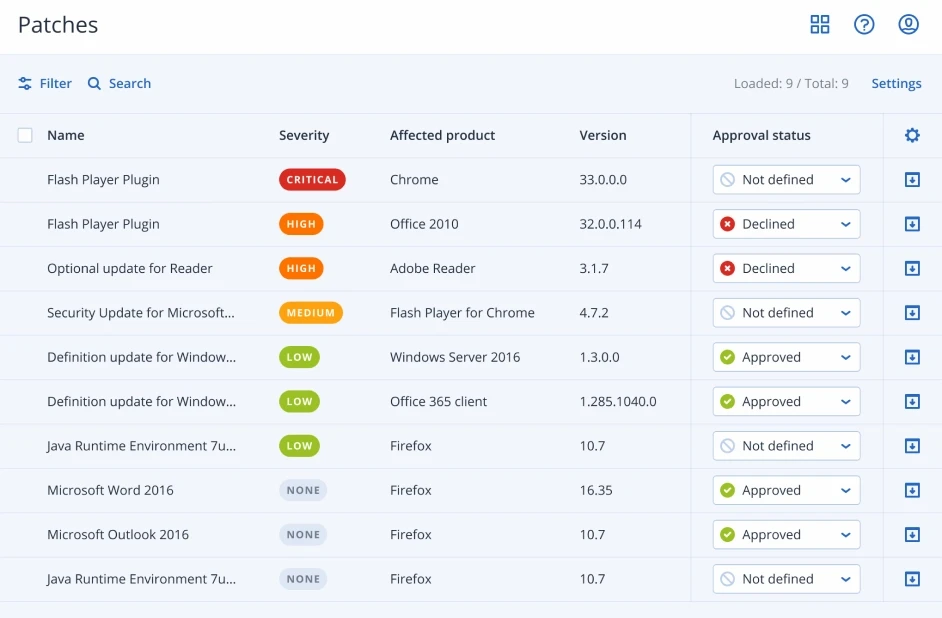
Endpoint Management
Automated patch management and easy work planning to reduce your administrative burden so you spend less time juggling solutions and more time protecting your data, applications, and systems.

"Technology is an integral part of our success in the sports business. With this reliance on technology comes a large risk of business disruption through the compromise of our data. We are happy to have a valuable partner in Bluefin and Acronis who are providing us additional peace of mind that our data is safe and secure."
Mike Webb, Vice President of Technology for the Jacksonville Jaguars
All-In-One Cyber Protection
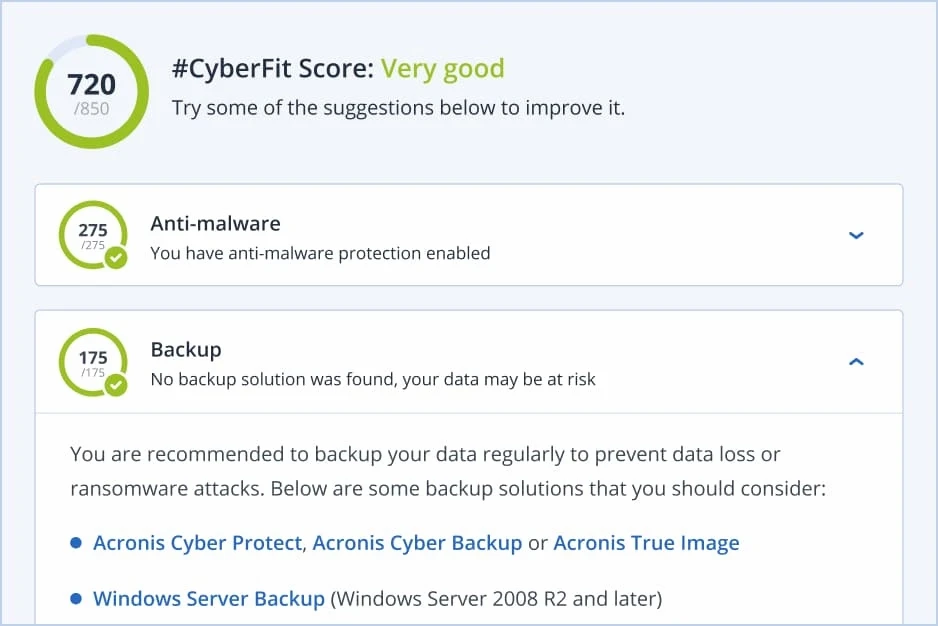
Integrated backup, recovery, and next-generation, AI-based anti-malware and protection management into one solution. This integration and automation provide complete cyber protection while increasing productivity and decreasing TCO. With one agent, one web-based management console, and one license, you can remove the complexity and risks associated with non-integrated solutions while benefitting from the five critical stages of cyber protection - prevention, detection, response, recovery, and forensics.
Prevention
Proactively protect your data, systems, and applications by preventing attacks from happening in the first place.
-
Antivirus and anti-malware
-
URL-filtering
-
Global threat monitoring
-
Continuous data protection
-
Patch Management
Detection
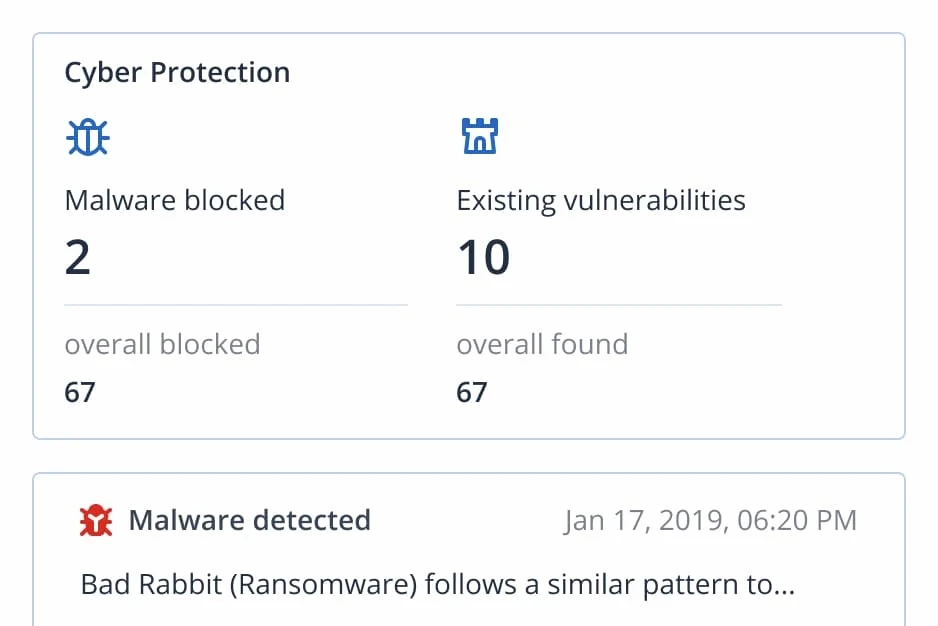
Detect issues and threats before they pose risk to an environment.
-
Vulnerability assessments
-
Virus and malware scans in the cloud
-
Hard drive health control
-
Dashboards and reports
Response
Enable quick action to minimize risk.
-
Cyber Protection Operation Center (CPOC) realtime alerts
-
Data compliance reporting and data protection map
-
Safe Recovery
-
Fail-safe patching
-
Malware quarantine
Recovery
Quickly and safely restore data in the event it gets compromised.
-
Instant Restore
-
Universal Restore
-
Safe recovery
Forensics
Mitigate future risks by collecting and performing forensic investigations.
-
Forensic backups
-
Audit support