Your Beacon in the Regulatory Fog
Making Compliance Management a Breeze
Full Steam Ahead: Navigating Compliance Easily
Staying compliant shouldn’t be overwhelming or time-consuming. At Bluefin Technology Group, we make Governance, Risk, and Compliance (GRC) management effortless for Jacksonville businesses, ensuring they stay ahead of evolving regulations and industry standards. Our compliance services help you reduce security risks, avoid costly fines, and build trust with clients—all while streamlining the process so you can focus on running your business.
Best of all, getting started is as simple as 1-2-3:
Chart Your Course with a Compliance Analysis
Start with a risk assessment to identify your exposure and create a clear plan based on industry best practices.
Navigate with a Custom Compliance Roadmap
Quickly roll out policies and procedures that keep your business on track and in line with regulatory requirements.
Stay the Course with Governance and Automation
Track and manage compliance efforts in one streamlined platform, ensuring ongoing success without the hassle.
Whether you need to qualify for government contracts, meet cybersecurity insurance requirements, or build trust with security-conscious clients, our risk and compliance solutions make it easy. Protect your business, enhance security, and stay ahead of industry regulations—all with an efficient, stress-free approach.
We Make Compliance ‘Business as Usual’
Does compliance make you feel overwhelmed? Are you stuck searching for documents in a messy SharePoint folder? Struggling to keep files current? Battling access issues? Whatever the pain point, Bluefin Technology Group’s Compliance Management Services are designed to simplify the process and untangle the compliance mess. By leveraging seamless asset governance, risk assessments, and policy management, we help you stay on track. Our Governance as a Service (GaaS) minimizes missteps, putting everything in one easy-to-access location. With our process, you can be confident your policies are Aligned, Authorized, Adopted, and Assessed. It’s compliance—simplified.
Alignment
Ensuring Policies Align with Your Business Goals
Aligning your policies and procedures with your business’s strategic goals is crucial for compliance success. This step ensures your governance practices support the broader mission and objectives of your organization. During the alignment phase, we identify how your policies can drive your business toward its goals, setting a strong foundation for seamless compliance.
Authorization
Securing Approval for Your Compliance Policies
Authorization ensures that key stakeholders review and approve every policy and procedure before implementation. This step involves obtaining the necessary approvals, signatures, and permissions to ensure your policies are recognized and accepted at all levels. With proper authorization, you guarantee that all policies are supported and backed by the necessary decision-makers.
Adoption
Fostering a Culture of Compliance
Once policies are authorized, the next step is ensuring they are adopted and embraced throughout your organization. Adoption involves communicating the policies clearly, providing training, and offering the resources needed for employees to follow them effectively. This step creates a culture of compliance, ensuring that everyone understands and adheres to the established policies.
Assessment
Keeping Policies Relevant, Up-to-Date, and Compliant
Continuous assessments ensure your policies and procedures remain effective and aligned with your organization's objectives. This helps identify gaps in compliance, pinpoint areas for improvement, and keep your documents relevant in an ever-evolving regulatory landscape. This is critical to monitoring progress and making adjustments to maintain alignment with your business's goals.
Simplifying Compliance. Building Confidence.
Compliance shouldn’t be a burden—it should be a natural part of doing business. At Bluefin Technology Group, we take the complexity out of Governance, Risk, and Compliance (GRC) management, helping businesses in Jacksonville and beyond meet industry regulations without the stress. Our streamlined compliance solutions ensure that policies aren’t just created but actively followed, reviewed, and continuously improved to keep your business secure and audit-ready.
Whether you need to qualify for cyber insurance, maintain compliance for government contracts, or meet security requirements for new business opportunities, our tools and expert guidance make the process simple. We remove the guesswork from risk management and regulatory compliance, so you can focus on growth while staying protected. With Bluefin as your compliance partner, you’ll have the confidence to operate securely and competitively in today’s business landscape.
Stay on Course with Active Governance
Compliance isn’t just about checking boxes—it’s about maintaining a strong foundation for security and risk management. Our Compliance Management Services ensures that policies, risk assessments, and security controls aren’t just created and forgotten. Instead, they are actively followed, regularly reviewed, and continuously updated to align with evolving regulations. By integrating GRC best practices, we help businesses in Jacksonville stay compliant while reducing risk exposure and strengthening their security posture.
Take the Pain Out of Documentation
Managing compliance documentation can be time-consuming and complex, but it doesn’t have to be. Our Policy Scorecard simplifies the process by offering pre-built starter policies, automation tools, and clear compliance guidance tailored to your industry. From cybersecurity policies to regulatory frameworks, we streamline compliance management, saving businesses valuable time while ensuring they remain audit-ready. Whether you're working toward cyber insurance approval or maintaining regulatory compliance, our solution eliminates manual effort and helps you stay ahead of compliance challenges.
Policy Packs for Every Destination
Meeting compliance standards is easier when you have the right tools at your disposal. Our Policy Packs are designed to help businesses comply with regulatory frameworks by providing industry-specific policies and procedures. Whether you're in finance, healthcare, defense, or another regulated industry, these organized packs simplify compliance management, reduce risk, and support contract eligibility for security-conscious partners and government contracts. With our comprehensive compliance tools, your business can maintain trust, meet industry standards, and operate with confidence.
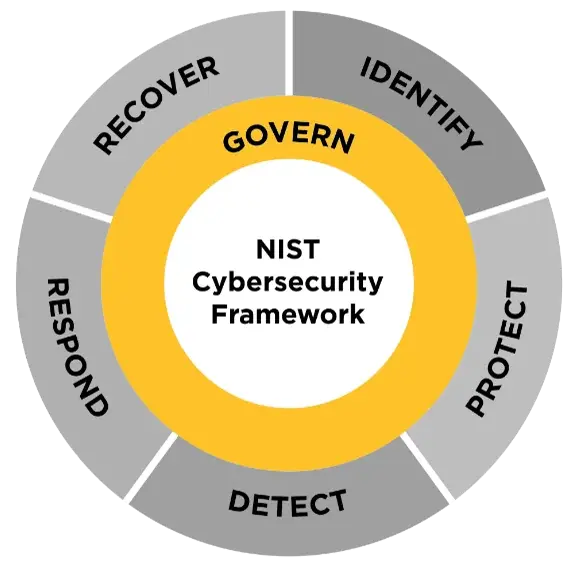
Ready-Made Compliance Framework
Keeping You Ahead of Regulations and the Challenges They Bring
 Business Risk
Business Risk
The Business Risk Assessment evaluates how different departments identify, manage, and mitigate risks that could impact operations. This framework helps organizations strengthen risk management strategies, improve resilience, and ensure long-term success.
 CCPA
CCPA
The California Consumer Privacy Act (CCPA) grants California residents control over their personal data, ensuring transparency in data collection, sharing, and deletion. This framework helps businesses stay compliant with privacy regulations and build consumer trust.
 CIS V8
CIS V8
CIS Controls v8 provides updated cybersecurity safeguards designed for modern environments, including cloud and hybrid systems. It enhances security, mitigates cyber threats, and aligns with industry regulations to keep your organization protected.
 CIS V8.1
CIS V8.1
CIS Controls v8.1 enhances cybersecurity with revised asset classes, updated Safeguard descriptions, and the introduction of the "Governance" function, aligning with NIST CSF 2.0 for stronger security management. These updates help organizations improve risk oversight and streamline compliance efforts.
 CMMC
CMMC
The Cybersecurity Maturity Model Certification (CMMC) ensures the protection of sensitive unclassified information for Department of Defense contractors and subcontractors. It establishes tiered cybersecurity requirements, helping organizations strengthen their security posture and meet federal compliance standards.
 COSO
COSO
The Committee of Sponsoring Organizations of the Treadway Commission (COSO) offers a comprehensive framework for enterprise risk management, internal control, and fraud deterrence. It helps organizations identify, assess, and manage risk while enhancing operational performance and regulatory compliance.
 Cyber Essentials
Cyber Essentials
A UK government-backed certification designed to strengthen cybersecurity by implementing five essential controls: firewalls, secure configuration, access control, malware protection, and patch management. This framework helps organizations protect against common cyber threats and demonstrate a commitment to cybersecurity best practices.
 DORA
DORA
The Digital Operational Resilience Act sets uniform security requirements for information systems of financial entities and critical ICT third-party service providers in the European Union. It ensures organizations can effectively manage ICT risks, enhance operational resilience, and maintain robust security, ensuring continued service delivery even in disruptive scenarios.
 Essential Eight
Essential Eight
The Essential Eight is a set of baseline mitigation strategies developed by the Australian Cyber Security Centre to enhance cybersecurity practices within organizations. These strategies are designed to help businesses protect against a range of cyber threats by implementing security controls, including application whitelisting, patching, and multi-factor authentication.
 FFIEC
FFIEC
Federally regulated financial institutions, holding companies, and non-financial subsidiaries must adhere to the technology standards set by the Federal Financial Institutions Examination Council. These standards ensure financial entities maintain robust risk management, cybersecurity, and operational resilience practices to safeguard financial systems from emerging threats.
 FTC GLBA
FTC GLBA
The Gramm-Leach-Bliley Act mandates that financial institutions disclose their information-sharing practices to customers while safeguarding sensitive financial data. This regulation aims to ensure the privacy and protection of personal financial information, requiring organizations to implement measures to secure customer data and prevent unauthorized access or disclosure.
 FTC Safeguards
FTC Safeguards
The FTC’s Safeguards Rule, updated in 2021, mandates that financial institutions implement robust security measures to protect customer information. This regulation provides modern, detailed guidance on safeguarding data, ensuring that entities under FTC oversight maintain secure systems to protect sensitive customer data from breaches and unauthorized access.
 HIPAA Privacy
HIPAA Privacy
The HIPAA Privacy Rule grants individuals the right to access and request copies of their health information from healthcare providers and plans. This rule ensures that individuals can direct copies of their health information to a third party, and it applies across all record formats and origins, safeguarding personal health data and ensuring privacy compliance.
 HIPAA Security
HIPAA Security
The HIPAA Security Rule establishes national standards for safeguarding electronic protected health information (ePHI). It outlines compliance obligations, defines protected data, and specifies the necessary security measures to implement the Privacy Rule’s protections, ensuring that sensitive health information remains secure and confidential in electronic form.
 ISO
ISO
Established by the International Organization for Standardization, the 27000 series sets global standards for information security management. These standards provide a comprehensive framework for organizations to manage and protect sensitive data, ensuring consistency and reliability in securing information systems while meeting compliance and regulatory requirements.
 NIS 2
NIS 2
The NIS 2 Directive establishes cybersecurity requirements for entities across the EU. It mandates comprehensive measures to manage and mitigate risks to networks, ensuring a high level of cybersecurity resilience and protection across critical sectors.. This directive aims to strengthen the overall security posture of the digital infrastructure vital to public safety.
 NIST CSF 1.1
NIST CSF 1.1
The NIST Cybersecurity Framework (CSF 1.1) provides a policy framework designed to help organizations assess and improve their ability to prevent, detect, and respond to cyberattacks more effectively. It offers a flexible, risk-based approach to cybersecurity, emphasizing the core functions of Identify, Protect, Detect, Respond, and Recover.
 NIST CSF 2.0
NIST CSF 2.0
The NIST Cybersecurity Framework (CSF) 2.0 is a voluntary framework that helps organizations of all sizes and sectors manage and reduce cybersecurity risks. This updated version introduces a stronger focus on governance practices. It incorporates new guidance to address evolving risks, regulatory requirements, and the increasing need for cybersecurity.
 NIST 800-53 Rev 5
NIST 800-53 Rev 5
NIST 800-53 Revision 5 provides a comprehensive set of security and privacy controls with an emphasis on privacy protection, resilience, and the importance of governance in achieving a strong security posture. These controls are organized into 20 families, ensuring organizations can tailor their cybersecurity efforts to meet both operational and compliance needs.
 NIST 800-66
NIST 800-66
NIST Special Publication 800-66 provides detailed guidance on implementing the HIPAA Security Rule, helping healthcare organizations and business associates better assess risks, while establishing safeguards, and maintaining compliance to keep electronic protected health information (ePHI) safe from threats and vulnerabilities.
 NIST SP 800-171
NIST SP 800-171
NIST Special Publication 800-171 defines security requirements specific to protecting Controlled Unclassified Information (CUI) in non-federal systems and organizations. It establishes 14 families of security controls, covering areas such as access control, incident response, and system integrity, ensuring that contractors and service providers meet federal cybersecurity standards.
 NY DFS 500
NY DFS 500
The New York Department of Financial Services (NY DFS) Part 500 is a cybersecurity regulation that mandates financial institutions to implement and maintain a robust cybersecurity program. It requires risk assessments, incident response planning, and continuous monitoring to protect sensitive data and ensure regulatory compliance.
 PCI-DSS Version 3
PCI-DSS Version 3
Payment Card Industry Data Security Standard is designed to enhance the protection of cardholder data. It introduced stricter security controls for policies, procedures, and network architecture, along with enhanced cybersecurity requirements to help businesses secure payment environments and prevent data breaches.
 SOC 2
SOC 2
SOC 2 is a certification framework developed by the AICPA that evaluates an organization’s controls related to security, availability, processing integrity, confidentiality, and privacy. It ensures that service providers securely manage customer data to protect the organization and its clients from security threats and compliance risks.
 Build Your Own
Build Your Own
Not every organization follows a predefined compliance framework, but strong governance is still essential. Our platform enables you to create and manage both IT and non-IT policies—ranging from cybersecurity best practices to HR, finance, and operational procedures. With built-in tracking for adherence, version updates, and policy acknowledgments, you can ensure alignment across your organization while maintaining a centralized, audit-ready system for policy management.
Talk Nerdy To Me
Charting the Latest In Cybersecurity Threats and Trends
Set your course by the stars of cybersecurity with 'Talk Nerdy to Me.' Within this vault of knowledge, you'll discover the latest currents in Jacksonville's cybersecurity landscape—offering astute, user-friendly intelligence to empower your business's digital defense.
3 min read
Microsoft Authenticator: It’s Not Overkill. It’s Overdue.
Erick Wilson: Jul 21, 2025
2 min read
MFA: Mother Freakin' Annoying — Until It Isn’t 😤🔐
Erick Wilson: Jun 4, 2025

